Zero Trust Authentication: What It Is & How to Achieve It



Until recently, Zero Trust was more popular with marketing teams than the security trenches. Although the concepts behind it encompass well-known security tenets, the terminology and approach as an organizing principle lacked widespread traction. The Zero Trust Mandate contained in the recent Executive Order on Improving the Nation's Cybersecurity and the OMB’s Zero Trust federal strategy, however, upped its visibility. Moreover, the rise in distributed workforces and recent publicized attacks, such as the Colonial Pipeline disaster, has made it eminently clear that old approaches no longer work.
What Is the Zero Trust Security Model?
The key principle behind the Zero Trust security model is to take a “never trust, always verify” approach in granting access to data and resources. It was introduced by analyst John Kindervag of Forrester in 2010 and, among other sources, has been codified by the National Institute of Standards and Technology (NIST) in NIST-800-207.
A Zero Trust security architecture assumes that there is no such thing as a “secure network perimeter,” with everything outside untrusted, but everything inside deemed trustworthy. By taking a primary position that any user or device could be compromised at any time, it rejects the idea of continuous or unlimited access to assets and replaces it with rigorous and ongoing Zero Trust Authentication.
The Role of Zero Trust Authentication
Under Zero Trust, there is no defined perimeter so trust must be based on a securely authenticated identity. This identity-centric model creates a critical need for strong authentication to ensure that only the right users gain access to the right resources for the right reasons.
Given that authentication acts as the gatekeeper into a Zero Trust security model, the Executive Order requires blanket adoption of multi-factor authentication (MFA). Best practices further dictate that this MFA be able to withstand phishing attacks in order to provide strong Zero Trust Authentication. This follows along the lines of the OMB guidance, which recommends phishing-resistant FIDO-based authenticators to meet Zero Trust authentication protocols.
As the need for Zero Trust Authentication is a constant between all parties, the process must be streamlined and non-invasive. Otherwise it will slow down workflows and frustrate users who may then seek to bypass security controls.
Challenges of Zero Trust Authentication
As with any shift in a security paradigm, there will be challenges, both on the technical side and for users themselves. Widespread adoption of Zero Trust security depends on overcoming these issues, which include:
- Passwords: Unfortunately, passwords are still part of many MFA systems despite being vulnerable to attacks such as phishing, account takeover, SIM-swapping and credential stuffing.
- Remote Zero Trust Authentication: Remote work has increased greatly in recent years, meaning viable Zero Trust security for remote entry points (VPN, VDI, RDP) is vital for risk reduction.
- Strong Authentication into Desktop: Logging in to an enterprise desktop and then subsequently having to log in via SSO or a separate authenticator in order to access resources creates a time-consuming redundancy. It can also cause integration issues.
- Secure Application Access: Integrating secure Zero Trust Authentication across all enterprise applications, especially legacy apps, can create considerable compatibility problems.
- Usability Issues: Added friction creates frustration and adoption resistance in users. It can also affect productivity and lead users to try to take shortcuts around Zero Trust security measures.
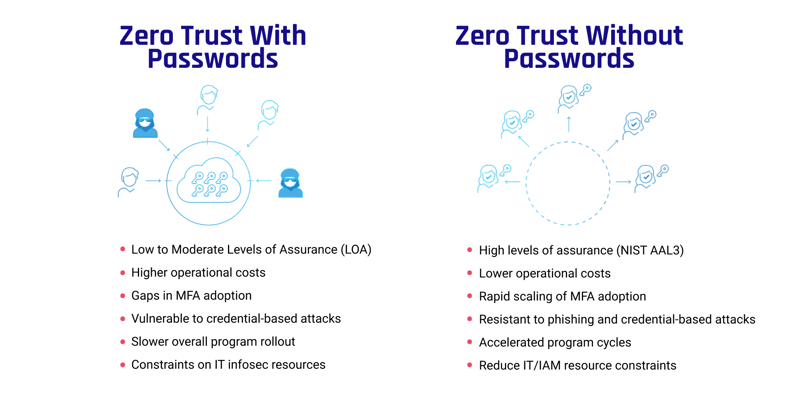
Is It Time for Businesses to Adopt Zero Trust Authentication?
The Executive Order and guidance from the OMB only apply to government agencies and contractors working with them. However, it’s an unspoken rule that government level directives soon become incorporated into more general regulations, audit checklists and other areas that impact the private sector. Many major enterprises, including Microsoft and Apple, are moving towards FIDO and adoption of passwordless authentication.
Regulatory pressures aside, there are enormous benefits to adopting Zero Trust Authentication. First, Zero Trust can help businesses be more agile. Zero Trust Authentication helps businesses leverage new technologies and take advantage of the full spectrum of deployment options for infrastructure, applications and data without the need to backhaul traffic through your network. Next, services can be delivered faster and more securely as there is less emphasis on where people, data and services are located and a greater emphasis on identity and context.
Successfully creating a Zero Trust security architecture is about integrating the necessary tools and practices, and being flexible enough to adapt to a shifting security paradigm. This means that Zero Trust security isn’t “one size fits all” and is a constant journey rather than a set-and-forget product.
HYPR Accelerates Zero Trust Security Initiatives
A cornerstone of any Zero Trust security initiative is phishing-resistant multi-factor authentication. Since MFA is the gatekeeper for the entire Zero Trust security ecosystem, the stronger that gatekeeper is, the stronger the security. However, gaps can occur, such as with dispersed workforces, remote employees or those traveling often. Often, this leads to the creation of exceptions rather than making those employees face multiple Zero Trust Authentication steps. These loopholes and adoption gaps can undermine your entire Zero Trust initiative.
By using FIDO security standards to underpin passwordless authentication, organizations can institute Zero Trust principles without adding friction to the user experience. It establishes the required trust of the user's identity, ensuring that your authentication processes align with the highest level of assurance (NIST 800-63B AAL3) and creating a solid foundation for your Zero Trust security architecture.
HYPR’s FIDO Certified passwordless MFA transforms users’ smart devices into PKI-backed security keys. It utilizes the hardware trusted platform module (TPM) and other device and OS-level security features to meet the phishing-resistant MFA requirements of Zero Trust.
We recognize that adoption and reducing friction are critical elements of a working Zero Trust environment, so our passwordless solution also focuses on easing the user experience, meaning our intuitive system can be deployed without training. Not only does this help bring about transformation more quickly, it does so at a lower cost and with reduced strain on security resources.
To find out how HYPR’s passwordless authentication can help support your journey to Zero Trust, download our white paper.
Related Content


