Passwordless authentication is a verification method that allows users to login to sites and applications without passwords. Instead, users can enter other identifiers. These could be tokens, biometrics, chips and cards, magic links, and more. Unlike password authentication methods, which require the user to remember their password, passwordless authentication does not require the user to remember verification factors. In addition, the user is verified with a unique factor at every login.
In its strongest forms, passwordless security solves several of the most persistent cybersecurity gaps today - poor password hygiene and centralized storage of credentials. We found in our report The State of Passwordless Security 2024, that 89% of organizations believe that passwordless authentication provides the highest level of security, making it essential to both the security and efficiency of their business.
In practice, the passwordless space is rapidly evolving, and the confusing terminology can make it difficult to understand what passwordless authentication is, the key principles, and how it functions in the enterprise. Whether you’re a seasoned security veteran or just getting started, this guide aims to simplify passwordless technology and will help you get started on your journey toward becoming a truly password-free organization.
What is the Problem with Passwords?
Passwords are inherently vulnerable because simple “username and password” combinations are easy to hack. Attackers can steal or guess passwords, and it doesn’t help that 64% of us re-use passwords across numerous accounts, so one hack equals instant access to multiple logins.
This means that passwords are a single point of failure that can be phished, brute-forced, or stolen in data breaches, opening the door to costly cyberattacks.
But even beyond security, the operational toll is significant: IT teams and employees spend valuable time on help desk support related to passwords, with some studies finding that password resets account for up to 40% of all calls.
Additionally, password management on the enterprise side often leads to centralized storage of credentials, requiring enhanced security controls such as hashing and other methods to prevent adversaries from breaking in and making use of these credentials. This burdens IT teams, wasting their time on issues that can be easily avoided. At the same time, it drains employee productivity since login issues delay work, de-focus employees from the task at hand, and harm morale.
Common Types of Password Attacks
- Brute force attacks: This involves an attacker attempting numerous passwords or passphrases with the aim of eventually guessing the correct one. Using automated attack tools, the attacker systematically tries all possible combinations of words, letters, and characters until a match is found. The longer and more complicated the password, the longer it takes. Often, they will use additional known data points, such as minimum password length or a requirement that it include certain characters, to increase their chance of success.
- Phishing: The practice of sending fraudulent emails, text messages, phone calls, or spoofed websites, disguised as legitimate ones, designed to persuade users to download malware or divulge personal information, such as a password or credit card number. Login credentials are the top target of phishing scams. Generative IA tools allow attackers to generate phishing lures that are highly personalized and convincing.
- Adversary-in-the-middle (AitM) attacks: In this attack, a perpetrator positions themself in a conversation between two parties — two users, two devices, or a user and an application or server — so that all communications are going to or through the attacker. Public WiFi is a popular vehicle for AitM. By breaching communications, the attacker can steal any shared credentials, payment card details, or other sensitive information.
- Credential stuffing: This type of attack leverages username and password combinations stolen in previous database breaches. Since many people reuse their passwords across different accounts, the attacker uses automation tools to inject the stolen username and password pairs into login forms en masse.
- Keylogging: Keystroke loggers capture keystroke information as a user types it in. They are often used in cyberattacks to steal sensitive information and credentials. When used maliciously, keyloggers are considered a type of spyware. However, keyloggers can also be used for legitimate purposes, such as troubleshooting issues on a device or monitoring children's computer use.
- SIM-swapping: Using personal information gathered through social engineering or other sources, the attacker convinces the victim's cell company to switch the phone number to a SIM card the attacker controls, usually by claiming the phone was lost or stolen. This means that attackers can use OTPs or account recovery information sent to that phone number to take over the victim’s accounts.
- Account Recovery: Where password guessing and advanced methods covered above prove challenging, adversaries will seek to target the weakest links in the identity chain of trust. At times, this may mean automated password reset processes that fall back to sending a temporary access code to an individual's email or answering knowledge-based questions. Calls to a helpdesk are also made to initiate a password reset cycle.
What Are the Different Authentication Factors?
There are three different categories of authentication factors: knowledge, possession and inherence, and it’s important to understand the differences between them before you attempt to understand the concept of passwordless security.
- Knowledge: In this category, you have to prove who you are with “something you know,” like a password or secret question.
- Possession: In this category, you have to prove who you are with “something you have,” like a security key, device, or one-time password.
- Inherence: In this category, you have to prove who you are with “something you are,” like a biometric fingerprint or facial scan.
Two-factor authentication requires using two such factors. Multi-factor authentication (MFA) requires two or more independent factors, meaning from two different categories.
Inherence, Possession, and Knowledge Factors
Passwordless authentication removes shared secrets or knowledge as an acceptable factor in the authentication process, as this category is most easily hacked. Instead, it only allows possession or inherence authentication factors. While it is possible for passwordless to be single-factor (ex, hardware security key), most passwordless solutions are multi-factor.
While passwordless should, in theory, mean authentication is free from passwords, some solutions provide a passwordless experience but still actually use passwords at some point in the process. For example, the user may verify their identity with biometrics on the front end, which is linked to a password that gets transmitted to a server on the back end.
Fully passwordless authentication solutions completely remove knowledge factors and shared secrets from authentication, and do not transmit or centrally store secret credentials.
Forms of Passwordless Authentication
There are several distinct forms of passwordless security authentication, each with varying levels of security, implementation complexity, and user experience considerations.
Basic Passwordless Methods
- Biometric Authentication: Using fingerprints, facial recognition, or voice recognition to verify identity, whilst pasting in the end user’s saved password following successful biometric authentication
- Hardware Security Keys: Physical devices like USB keys that store cryptographic keys
- Mobile Authenticators: Smartphone apps that generate or store authentication credentials
- Smart Cards: Cards with embedded chips containing unique cryptographic information
Usage of Passwordless Methods
- QR Code-Based Authentication: Instead of the traditional username entry in Step 1, users scan a QR code with their mobile device, which initiates the authentication flow directly
- Push Authentication: Authentication requests are sent directly to a pre-registered device, requiring only approval rather than active credential entry
- Context-Aware Authentication: Systems that evaluate multiple factors, including device, location, and behavior patterns, to authenticate without explicit user action
- Continuous Authentication: Ongoing verification throughout a session based on behavioral biometrics and usage patterns
How Does Passwordless Authentication Work?
The goal of “gold standard” true passwordless authentication, namely the Fast Identity Online (FIDO) specifications, is to completely remove shared secrets from the authentication process. Under FIDO and the expanded FIDO2 standards, authentication between the user and server is done through public key cryptography.
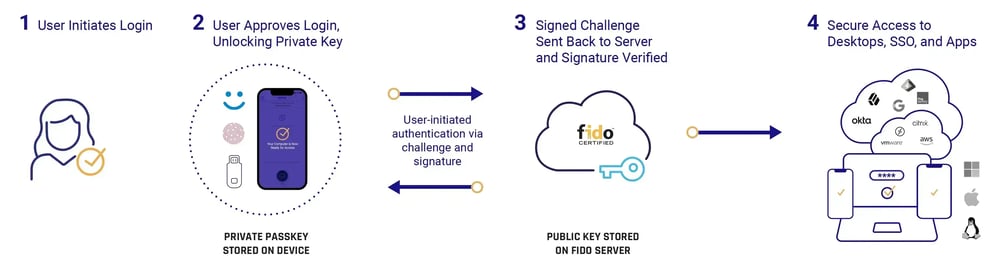
The Passwordless Login Flow Explained
Step 1: The user begins the login process, which sends an authentication request to the server.
Step 2: The authentication system challenges them to provide the required factors.
Step 3: A secure local action on the user's device, such as providing a face scan or thumbprint or using a security key, will unlock the private key.
Step 4: The private key is used to sign the challenge, proving user possession.
Step 5: The authenticating server verifies that the signature matches the stored public key.
Step 6: Upon a successful match, the user is authenticated for entry to the system.
In short, a user’s biometric features (inherence) unlock a private key on their device (possession) through an authenticator. Using cryptographic exchange protocols, this private key is matched with the public key of the partnership, verifying the user’s identity without sharing secrets or needing server-side databases.
Common Passwordless Login Methods
There are multiple password-free authentication methods, some relying on software, some on hardware. As mentioned earlier however, some solutions provide login methods that seem to be passwordless but actually use some form of shared secret and therefore can be breached, hacked or intercepted. One-time passwords (OTPs), magic links and even some biometric authentication methods fall under this category and technically are not passwordless.
Common passwordless authentication methods include:
- Push notifications: Authentication via a push notification sent to a user’s registered device (usually via a mobile app), which the user approves or denies. This may or may not be phishing-resistant, depending on the implementation.
- Biometric FIDO/FIDO2 Authenticators: Authentication via user biometrics (fingerprint, facial recognition) inputted at the device level and tied to a FIDO2 keypair.
- Passkeys: Allowing the user to identify at the device level with biometrics, PIN code, or other device mechanisms.
- Hardware security keys: A physical key (like USB/NFC) that performs cryptographic authentication.
- Windows Hello Passwordless: Signing up to Windows with biometric or PIN-based login.Smart cards (PIV) - Cryptographic cards issued by organizations (often government) that require card + PIN.
- Magic links: The User receives a time-limited login link via email. Clicking the link authenticates them.
- QR code authentication: A QR code is scanned using a mobile app tied to a trusted device. Authentication happens via cryptographic exchange.
Passwordless with SSO/MFA Integration
Passwordless authentication can either augment or replace traditional MFA mechanisms. Here's how it works with SSO and MFA:
- SSO Integration: Passwordless can be used as the primary authentication method into the SSO provider (e.g., Azure AD, Okta). Once authenticated, the user is authenticated through SSO into multiple apps without further login.
- MFA Integration: Passwordless methods can satisfy MFA requirements if two or more passwordless factors are inherently involved (e.g., biometrics + device possession.
Of course if any of these are used in combination with a password as a factor, then they are no longer passwordless.
| Method | Security | Phishing Resistance | Cost | Scalability | User Experience | Integration Complexity |
|---|---|---|---|---|---|---|
| Push Notifications | Moderate-high | Low–Moderate | Low–Med | Medium | Medium | Low |
| FIDO2 Biometrics | High | Strong | Low–Med | Medium | Medium | Medium |
| Passkeys | High | Strong | Low | High | High | Low–Medium |
| Hardware Security Keys | Very High | Very Strong | High | Low | Low | High |
| Windows Hello | High | Strong | Medium | Medium | Medium | Medium |
| Smart Cards (PIV/CAC) | Very High | Strong | High | Low | Low | High |
| Magic Links | Moderate | Low | Low | High | High | Very Low |
| QR Code Authentication | High | Strong | Medium | Med-High | High | Low–Medium |
The Pros and Cons of Passwordless Security Solutions
Passwordless authentication eliminates many of the challenges associated with legacy authentication methods. However, like any technology, it has pros and cons. Consider each when deciding if moving to passwordless technology is right for your organization.
The Benefits of Passwordless Authentication Solutions
Passwordless has several unique benefits over other types of authentication, including:
- Enhanced security: Passwords are the root cause of most cyberattacks; per Microsoft, there are over 18 billion password attacks a year. Getting rid of passwords drastically lowers your authentication risk profile.
- Improved user experience: Forgetting passwords and going through password resets are major sources of user frustration. Modern passwordless solutions can securely authenticate a user in seconds with something they almost always have in their possession (a personal device or biometric feature).
- Reduced IT costs: Password-based systems place a heavy burden on security teams, who must set and inform users about policies, ensure high levels of security around storage, and manage resets. The costs are significant, with password resets and other password-related issues costing companies an average of $375 per employee annually.
- Increased productivity: Login processes, including failed attempts, trying to remember a password, and resetting passwords, take up an average of three working days per employee. Simplifying the process with a passwordless solution improves access times, condensing multiple steps into a single action.
How To Solve Common Challenges when Going Passwordless
As with any technology and any significant change, passwordless authentication can bring potential challenges. These will vary depending on the type of passwordless solution and the organization’s IAM and IT environment. Areas to consider include:
Costs: Passwordless authentication that relies on hardware security keys introduces costs for the security keys and their ongoing management.
How to Solve This: You can choose a passwordless solution that relies on a mobile app and FIDO rather than a hardware key. But it’s important to measure not only the tool cost, but expected ROI and productivity gains. For example, cost savings related to reduced help desk costs, fewer account lockouts and downtime, the lower risk of phishing, reduced MFA fatigue, heightened employee morale from the user experience, faster onboarding and access, and more.
Expertise: Many IT teams have years of experience troubleshooting password-based systems, which are relatively straightforward.
How to Solve This: Choose a passwordless authentication vendor that’s intuitive and IT-friendly. Look for solutions that integrate seamlessly with your existing identity infrastructure, offer a clean and navigable admin interface, and include strong documentation and support.
Change Management and Delayed Adoption: Despite being a source of frustration, most people are comfortable with passwords. While passwordless authentication is more convenient in many ways, many people are not yet familiar with it, and there continues to be a perception that a password known to the end user is safely retained only in their memory, despite it being guessable by an adversary.Customers and employees will need time to transition to a new method of authentication.
How to Solve This: Make sure your passwordless methods are easy to use, and employing a clear change management strategy will increase adoption rates. You can follow these methods:
- Map Out Use Cases - Identify different teams, the systems, IdPs, devices and browsers they use, and their authentication requirements.
- Plan for Legacy Systems and Challenges: Evaluate compatibility with older apps and logins and prepare integration efforts.
- Strategic, Phased Rollout - Start small with pilot groups including tech-savvy and non-tech users, with execs onboard early. Then, iterate gradually, fine-tuning based on feedback before wider deployment.
- Communicate Clearly - Explain benefits and privacy practices, provide continuous training and use user-friendly messaging.
- Onboard Users and Offer Support Ensure help desk readiness across time zones or for traveling staff. Track metrics like login speeds, help tickets, user satisfaction pre/post-launch.
- Choose the Right Solution - Evaluate FIDO‑certified vendors and ensure comprehensive coverage, including recovery flows (lost/stolen devices, registration phases), and assess identity-proofing capabilities beyond initial authentication.
Scalability: A solution that works for 100 users may not scale securely and efficiently to thousands across multiple geos, platforms, and device types.
How to Solve This:
- Choose a federated identity platform that supports FIDO, enabling centralized policy control across geographies and device types.
- Automate user and credential lifecycle management to ensure efficient onboarding and recovery processes.
- Build scalable recovery flows and adaptive, risk-based authentication to help maintain security without creating friction.
- Continuously monitor adoption metrics and login performance for data-driven adjustments as the rollout expands
How Passwordless Technology Works with Passkeys and Zero Trust
Passkeys are a phishing-resistant replacement for passwords developed by the FIDO Alliance. There are two primary types: synced and device-bound. Synced passkeys can be used on multiple devices without re-enrolling each device. Since 2022, Apple, Google, and Microsoft have been rolling out support for synced passkeys across their various OSes.
On an enterprise level, device-bound passkeys are generally preferable as they can include features and controls that consumer passkeys do not. The HYPR authenticator is an example of a FIDO device-bound passkey that can be used for desktop access and integrates with the enterprise's overall technology stack.
The cornerstone of any Zero Trust security initiative is passwordless phishing-resistant multi-factor authentication as defined by the OMB, CISA and other security frameworks.
By using FIDO device-bound passkey security standards, organizations can institute Zero Trust authentication principles without adding friction to the user experience. It establishes the required trust of the user's identity, ensuring that your authentication processes align with the highest level of assurance (NIST 800-63B AAL3) and creating a solid foundation for your Zero Trust security architecture.
Note that synced passkeys do not provide this same level of assurance. Moreover, organizations will need to make sure they address all use cases, such as dispersed workforces, remote employees or those traveling often.
What To Look For in a Passwordless Solution
Not all passwordless solutions are equal, and many don’t offer the same levels of security. Furthermore, some solutions aren’t even “true” passwordless; these subpar solutions remove the shared secrets from the user’s view but still use them on the backend.
Passwordless Authentication Use Cases
Passwordless security allows organizations to enhance both security and the user experience. Here are some common use cases where passwordless authentication offers significant advantages:
- Workstation Logins: In large organizations, passwordless authentication can allow employees to log in to personal or joint workstations in a secure and easy manner. Passwordless security reduces the risk of phishing attacks or internal threats (whether malicious or inadvertent) and helps enforce the principle of least privilege.
For example, a top-five financial institution employed passwordless authentication for both Windows and Mac workstation logins, eliminating the need to remember long passwords while providing strong user-based MFA. This allowed employees to log in with their own unique credentials and permission levels, even on shared workstations.
- Customer Login for Online Service: Customer-facing applications, from banking apps to e-commerce sites to social media platforms, can leverage passwordless authentication for users. This simplifies the login process, which helps create a better customer experience and enhances usability. It also helps protect private data, which is important for building customer trust, safeguarding customer information, and meeting compliance regulations.
- Mobile and Web App Security - With the proliferation of mobile apps, passwordless methods such as biometric authentication (Face ID, Touch ID) can streamline the user experience and provide two layers of security. First, breaching the application if passwords are cracked. Second, protecting from malicious access and data theft from the app if the device itself is compromised.
For example, Ireland’s largest health insurer implemented passwordless authentication for their consumer-facing mobile applications, simplifying and improving the user experience.
- Remote Work and Virtual Access: As remote work becomes more common, organizations can use passwordless authentication methods to ensure secure remote access to corporate resources. This allows the organization to maintain control and governance over remote users and identities, whether they are accessing from public or private networks, or managed or unmanaged devices.
- Financial Transactions and Digital Payments: Financial services adopting passwordless authentication can better protect sensitive transactions. Passwordless makes the process much quicker and reduces the risk of fraudulent activities.
If you’re investigating passwordless authentication solutions, here’s a checklist of essential capabilities to look for:
✓ Completely removes shared secrets (passwords, OTPs), even for fallback flows
✓ Provides phishing-resistant desktop login as well as web apps
✓ Declutters the user experience and reduces login friction
✓ Uses the hardware Trusted Platform Module (TPM) or Secure Enclave to store private keys and other sensitive data
✓ Easy to deploy for IT teams
✓ Supports secure authentication for remote workers and works offline
✓ Integrates with major identity providers (IdPs) and devices
✓ Intuitive for users to learn and adapt to
✓ FIDO Certified for all components
✓ Achieves compliance with Zero Trust architecture and regulatory obligations
✓ Reduces the overall total cost of ownership (TCO) for authentication security
Passwordless Security Evaluation Guide
Organizations across all sizes and sectors are looking to passwordless technologies to make their authentication processes more secure while reducing friction.
This guide will help you assess passwordless security products and determine which solution best suits the needs and requirements of your organization.
Go Passwordless with HYPR’s Identity Security Solution
HYPR is the leader in passwordless identity assurance, delivering the industry's most comprehensive end-to-end identity security for the workforce. By unifying the strongest authentication, comprehensive risk monitoring, and enhanced identity verification, organizations can detect, prevent, and eliminate identity-related risks at every point in the user journey.
HYPR’s Identity Assurance platform consists of:
- HYPR Authenticate: Industry-leading FIDO2 Certified passwordless authentication. This replaces passwords and shared secrets across all user populations, applications, and locations. HYPR
- HYPR Adapt: Real-time risk assessment and adaptive security controls that assess risk from a broad and diverse set of sources, including user behavior, mobile, web, and browser signals, and changes in the overall threat landscape.
- HYPR Affirm: Automated and ongoing identity verification integrated into identity management and help desk workflows, without using passwords.
Passwordless FAQs
Yes. Passwords are the greatest threat to authentication security, and credential-related attacks are the biggest cyberattack vector. Unlike traditional MFA, passwordless MFA does not allow the use of passwords or other shared secrets to log in, making it a much safer solution
MFA, on the other hand, requires two or more factors, while one of these factors can be a password. This means MFA adds a security layer to passwords, while passwordless removes passwords, which are the weakest link, entirely.
The safest authentication method is the one that’s most difficult for attackers to bypass. Passwordless solutions such as biometric identifiers or unique key cards would require a dedicated attempt to acquire those specific details, which costs far more time and money than most attackers are willing to spend.
Passwordless authentication can be implemented in several ways. It can be integrated with your current authentication system through your solution’s SDK or integrated with your Single Sign-On (SSO) provider. Physically, hardware such as security keys, dongles, or hardware biometric identifiers can be rolled out directly but can be expensive to scale.
While there is no way to completely stop a determined attacker, fully passwordless authentication — where there is no password or other shared secret between the person and the service — is far more secure than password-based authentication.
The FIDO Standards are a set of open authentication protocols that govern the implementation of user-friendly, passwordless authentication solutions developed to ensure security, interoperability and scalability. The Fast Identity Online (FIDO) Alliance is an industry association that includes some of the biggest names in tech and finance as well as regulatory bodies like the National Institute for Standards and Technology (NIST).
FIDO2 combines the specifications for the FIDO Alliance’s Client-to-Authenticator Protocol (CTAP) and the World Wide Web Consortium’s (WC3) Web Authentication (WebAuthn) specification. WebAuthn is a standard for authenticating users to web applications, allowing users to securely authenticate themselves without their information ever being passed to the website or application.
FIDO Certified products are software solutions that have undergone rigorous testing around security, usability, and scalability. Certification by the FIDO standards body, or lack thereof, speaks to a solution's enterprise readiness and deployability. While all FIDO Certified products adhere to similar standards, the solutions vary in speed, usability and accessibility. Read the FIDO guide to learn more about comparing FIDO products.
This will depend on the passwordless solution. Strong Customer Authentication (SCA) requires MFA to be deployed, utilizing “separated software execution environments.” FIDO Certified true passwordless authentication is inherently multi-factor, combining a strong possession factor with local user-inherent factors, with all cryptographic materials stored and processed in the device trusted platform module (TPM).
Again, this will depend on the passwordless solution. In theory, passwordless security supports organizations in achieving a Zero Trust security model by removing one of the biggest trust issues in authentication (passwords). Specifically, the OMB stipulates the use of phishing-resistant MFA to meet Zero Trust authentication requirements. Moreover, the passwordless solution should cover all organizational use cases including desktop and server access, remote entry points (VPN, VDI, RDP) and enterprise applications.
You’ve probably heard of multi-factor authentication (MFA), which shares some of the same objectives as passwordless authentication. There are, however, some distinct differences between passwordless and MFA. MFA allows users to verify their identity with any of three factors (knowledge, possession, inherence), whereas passwordless authentication generally only accepts possession and inherence factors (in some cases a local device PIN may be used in place of, or in addition to, a biometric).
Also, importantly, many passwordless solutions, especially those built on FIDO standards, have recognized user friction as a key source of security lapses. As such, most passwordless solutions have a strong “user friendliness” objective, which is absent from many MFA models.
This approach fundamentally changes the attack surface - instead of trying to guess or steal credentials, an attacker would need physical access to both a user's device and their biometric data or PIN, making large-scale remote attacks virtually impossible. Other advantages include:
Asymmetric Cryptography: Unlike passwords which are shared secrets, PKI uses a pair of mathematically related keys - one public, one private. The private key never leaves the user's device, eliminating the risk of server-side credential breaches.
Phishing Resistance: Since authentication is based on cryptographic challenges rather than shared knowledge, phishing attacks become ineffective - attackers cannot use stolen credentials because they need the physical private key.
No Transmission of Secrets: During authentication, no secret information is transmitted over the network, only cryptographic proofs that can't be replayed or reused.
Decentralized Security Model: Private keys are distributed across user devices rather than stored in a central repository, eliminating the "one breach compromises all" risk of password databases.
Non-Reversibility: The cryptographic operations used in PKI are practically impossible to reverse, unlike password hashes, which can potentially be cracked.