Solutions Workforce Identity Verification Audit
No-Deployment Workforce Identity Verification Audit
Run the audit. Get the truth.
Take action – all in a day, not months.
Fast, Secure, and Streamlined Identity Audits
-
Comprehensive Verification: Employs multi-factor identity verification techniques, including document authentication, facial recognition with liveness detection, device verification, and location checks, for maximized assurance.
-
No Deployment Needed: Designed for a specific scope (e.g., verifying a specific number of employees) with a streamlined, point-in-time process requiring no deployment with in-house systems.
-
Streamlined Process: Automates and simplifies the identity verification process, reducing manual effort and improving efficiency for administrators and employees.
-
Actionable Insights: Delivers clear results and a detailed audit trail, crucial for compliance reporting and internal security reviews.
-
Meet Compliance Needs: Helps organizations meet stringent compliance requirements and Know Your Employee (KYE) controls with robust identity proofing.
Fraud is a Systemic Threat, Handled in Silos
Most teams discover identity fraud by accident. A suspicious resume. A Zoom glitch. A feeling that something’s off. But these one-off catches only scratch the surface.
Meanwhile, the rest of your workforce is operating on trust and assumption, without proof of who they really are.
- 95% of organizations have experienced a deepfake or impersonation attempt
- AI-generated profiles and spoofed locations bypass traditional background checks
- North Korean operatives have posed as legitimate IT workers inside U.S. companies
The cost? Fraudulent employees can quietly drain $80K+ per hire, expose sensitive systems, or worse - never get caught.
.jpg?width=1378&height=895&name=HYPR-locationverified-1378x895%20(2).jpg)
What the HYPR Identity Verification Audit Delivers
Effortlessly verify your entire workforce through a multi-factor identity workflow, equipping your team with a clear, actionable report to uncover hidden risks and confirm workforce authenticity.

Device Verification: Confirming the device used for verification.
Location Checks: Comparing geolocation against expected locations where appropriate and permissible.
Document Verification: Verifying official documents like driver's licenses or passports with advanced forgery detection and database lookup.
Facial Recognition: Utilizing cutting-edge technology with liveness detection to match the individual to their provided documents.
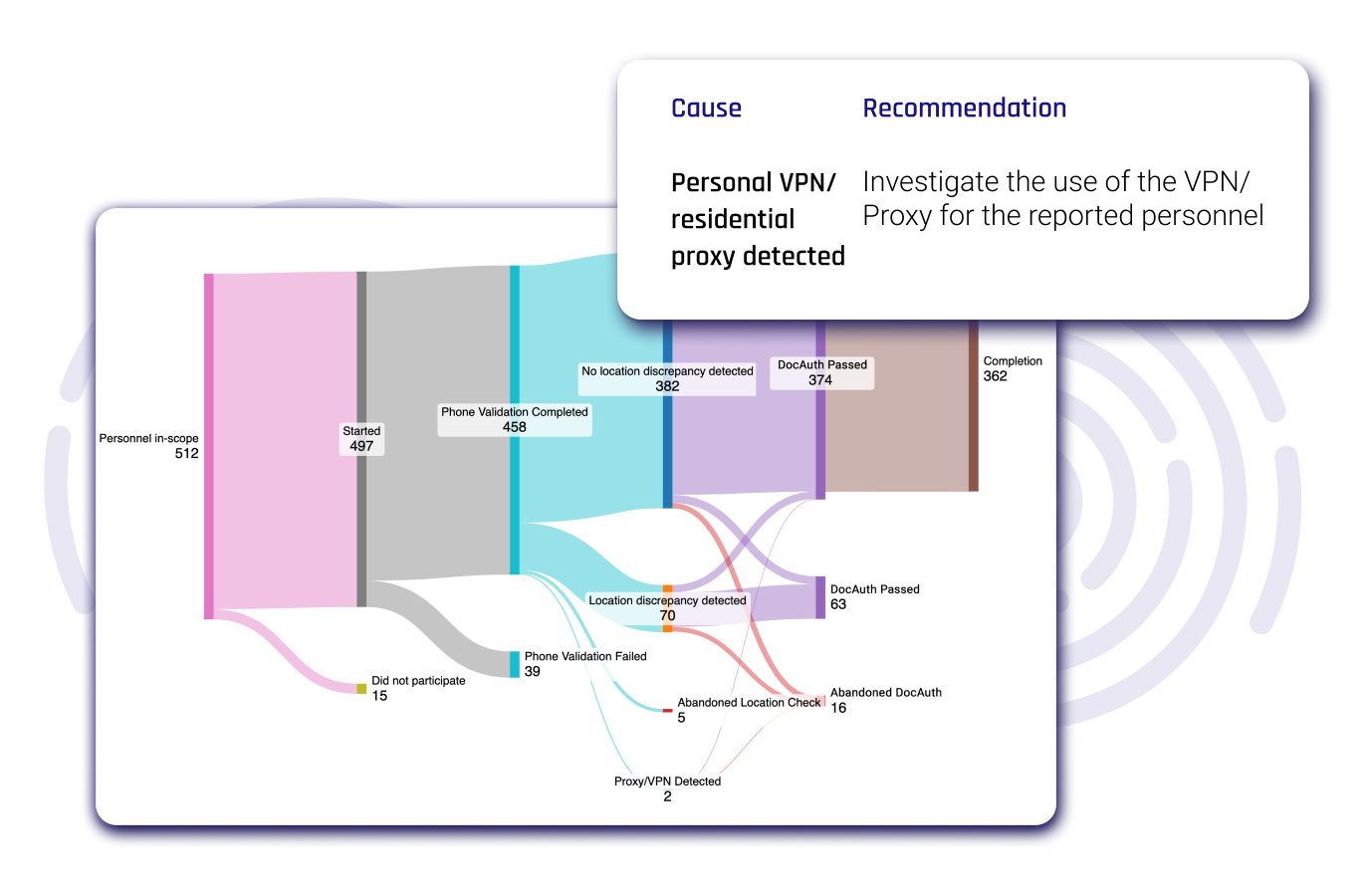
Your Individualized IDV Audit Report
Following the completion of your HYPR Workforce Identity Verification Audit, we will provide you with a comprehensive and individualized report.
The purpose of this tailored report is to:
- Identify potential frauds or risks specifically associated with the identity information of your current employees.
- Offer actionable recommendations for improvements to enhance security measures surrounding your employees.
Why Choose HYPR Affirm for Your Identity Verification Audits?
- Proven Identity Verification Expertise: HYPR leverages a deep understanding of identity challenges and proven methodologies to combat sophisticated cyberthreats. Our solutions are trusted by large, complex organizations, including 2 of the 4 largest US banks, and organizations of all sizes and sectors globally.
- Leaders in Identity Assurance: As experts in identity assurance, we ensure users are who they claim to be throughout the identity lifecycle. HYPR Affirm exemplifies this with its thorough and configurable verification approach.

What Our Customers Are Saying About Us
-

HYPR has made the login experience seamless for my team. It was quick and easy to set up for our Okta users, and I appreciate that we can configure it to allow users to log in once at the workstation level, then seamlessly access our SSO without needing additional authentication.
IT User -

HYPR is easy to manage. My end users love using HYPR to login to their computers.
Shane C.Cybersecurity Administrator -

The multifactor solution for iPhone and Android is bar none for corporate environments. Users have one app for all their MFA. Integrates with all of our tools using SAML.
Manufacturing User -

The team at HYPR goes above and beyond to make sure our deployment is successful. The focus on end user experience is key.
Financial Services User -

I like how HYPR works across multiple platforms seamlessly. I use it on a daily basis with my iPhone and work computer.
Automotive User

Related IDV Resources
Let’s See Who’s Really in Your Workforce
Request your audit today and expose identity fraud before it becomes your next crisis.
No software. No commitment. Just clarity.




