Solutions Zero Trust Authentication Built on Passkeys
Stop Credential Attacks with Zero Trust Authentication Built on Passkeys
Remove Authentication Friction and Reduce Your Attack Surface
Accelerate your Zero Trust strategy with strong, frictionless authentication
based on FIDO Certified passkeys.
Solve Your MFA Gaps
Simple, Friction-Free User Experience
Continuous Security at the Highest Level of Assurance
Zero Trust Authentication Challenges
Zero Trust initiatives can be derailed by technical obstacles and users themselves. Meaningful adoption of Zero Trust security depends on overcoming these issues, which include:
- Gaps in phishing-resistant MFA for desktop login, VDI, VPN, RDP and other edge use cases
- Poor user experience that creates adoption resistance
- Integration of secure Zero Trust Authentication across all enterprise applications, including legacy apps
- Decreased productivity due to added friction
- Compliance risks if methods do not conform to data residency provisions and other requirements of regulations such as GDPR
Zero Trust Needs Zero Passwords
A Zero Trust strategy rests on securely authenticated identity. HYPR provides continuous, rigorous Zero Trust Authentication while removing user friction. With HYPR, you can drive transformation more quickly, at a lower cost, and with reduced strain on security resources.
Eliminate credential-based breaches
Reduce your attack surface. EasilyReplace passwords and other shared secrets with passkeys that remain in the most secured areas of the user device at all times.
Authenticate using two strong factors in one single gesture and enforce risk-based, step-up authentication policies.


Accelerate Zero Trust Adoption
Deploy authentication that people want to use. HYPR unifies siloed identity systems and combines multiple authenticators into a single user action. Users login only once to safely access organizational resources, desktop to cloud.
Learn how Kinaxis deployed passwordless to drive their Zero Trust program in this on-demand webinar.
Meet Zero Trust Compliance Guidelines
Ensure your authentication processes align with regulatory guidance and Zero Trust security frameworks. HYPR Authenticate adheres to NIST AAL3 and is FIDO Certified on all components, meeting the gold standard for Zero Trust authentication defined by CISA and other regulatory agencies.

Comprehensive Adaptive Authentication
HYPR Adapt adds risk-based, adaptive authentication so you can manage identity-related risks and reduce user friction, even in rapidly changing security environments. It continuously assesses risk from a broad and diverse set of sources, dynamically adjusting Zero Trust authentication controls on an individual user basis.

A Zero Trust security initiative built on top of passwords is like a house of cards. HYPR's passwordless MFA solution solves that problem and has given practitioners a solid foundation upon which they can build a world-class security program.
Taylor Lehmann
CISO, Google Cloud
Zero Trust Authentication in One Simple Action
What does Zero Trust authentication with HYPR look like?
For example, your employee first logs into their computer with passkey-based desktop multi-factor authentication.Then, if there are no risk signals triggered, they automatically are authenticated into your corporate SSO. If they require access to a more sensitive app or if their risk profile changes, they can be prompted for step-up authentication.

Related Zero Trust Authentication Resources

A Journey to Zero Trust with Zero Passwords
You're ready to implement a Zero Trust architecture, but how does passwordless MFA fit in?

Complying with Cybersecurity Executive Order Zero Trust
Learn about the mandate that agencies deploy MFA to enable a Zero Trust architecture.
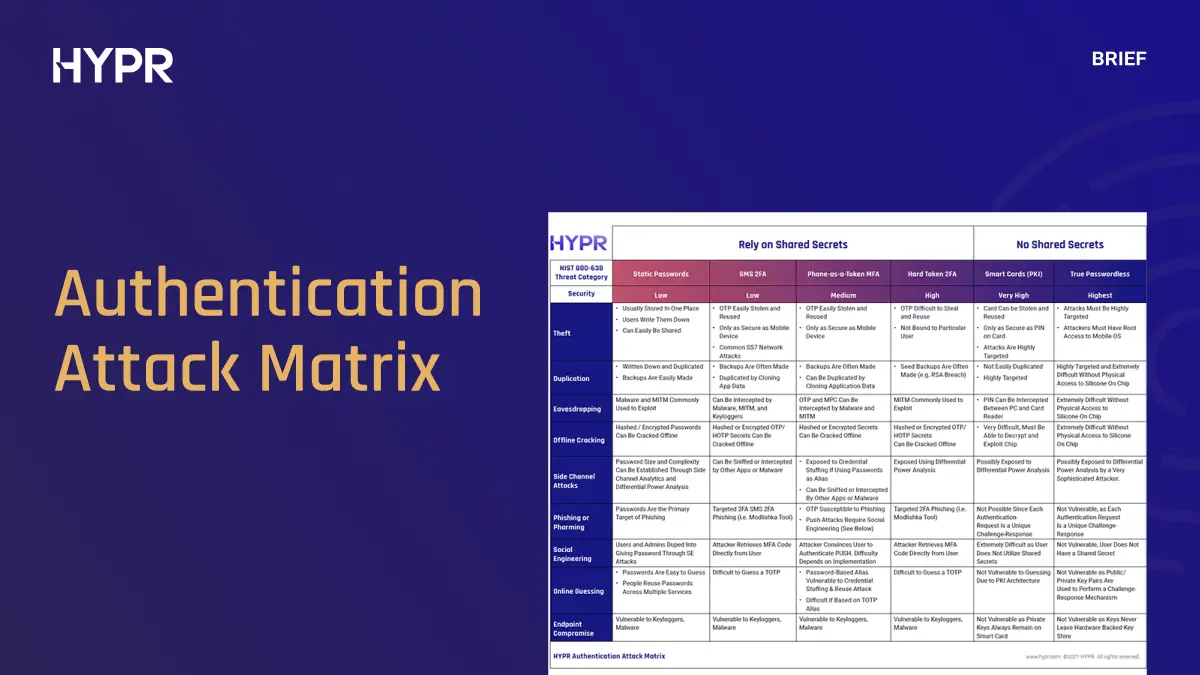
NIST Authentication Attack Matrix
The Authentication Attack Matrix heat-maps threats against various authentication modalities.

Zero Trust Authentication: What It Is & How to Achieve It
Learn about Zero Trust authentication and why it's critical to a Zero Trust security model.
Request a Demo
Experience passwordless MFA that secures and empowers your business. See what identity verification built for the workforce looks like. Learn how comprehensive Identity Assurance protects the entire identity lifecycle.
Fill out the form to get a demo from an identity security expert, customized around your organization’s environment and needs.







