Resources
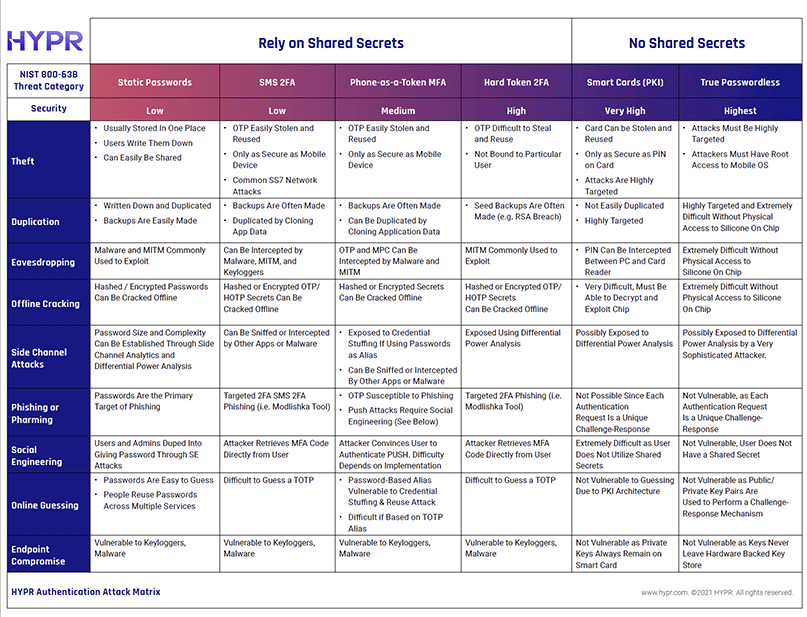
Authentication Attack Matrix
Authentication Attack Matrix
2FA, MFA, Soft Tokens, Hard Tokens, Passwordless, Smart Cards – your users have more ways to log in than ever before. With so many authentication methods available, how do various approaches compare to one another? The Authentication Attack Matrix heat-maps known security threats against various modalities and is offered to arm executives security practitioners with added knowledge on which to base critical authentication sourcing decisions.