Passwordless Login Methods
There are many ways to authenticate without a password. Software-based approaches typically utilize a mobile app on a smartphone alongside a biometric authenticator such as iOS Touch ID. Hardware-based methods include smart cards and physical security tokens. Native or built-in authenticators such as Windows Hello may also be classified as hardware-based approaches as they require specialized devices and biometric sensors.
Practitioners have many different options to implement a passwordless experience, each focused on reducing hard and soft costs, as well as to improve productivity of both users and IT operations teams. Below, we analyze the pros and cons of several technology options for buyers to hopefully simplify some of the decisions in the shift to passwordless authentication.
FIDO2 Mobile and Web Login
This category includes the use of smartphones for accessing mobile, web and desktop applications. Specifically, they cover the use of FIDO authentication when made possible with a mobile/web app or SDK.
Most common is the use of mobile authenticators such as Apple Face ID and the many different biometric authenticators available on smartphones today across iOS and Android.
It may also include the use of built-in biometrics, also known as "platform authenticators" such as Windows Hello and MacOS Touch ID.
It's important to note that simply utilizing the biometric authenticator on a device is not sufficient for going passwordless. Smartphones typically link a biometric to a user password but do not eliminate the actual password. That's why organizations adopt passwordless software solutions in order to bridge the gap between a person and the login experience. These solutions combine the use of a biometric smartphone with public-key encryption and open standards such as FIDO2.
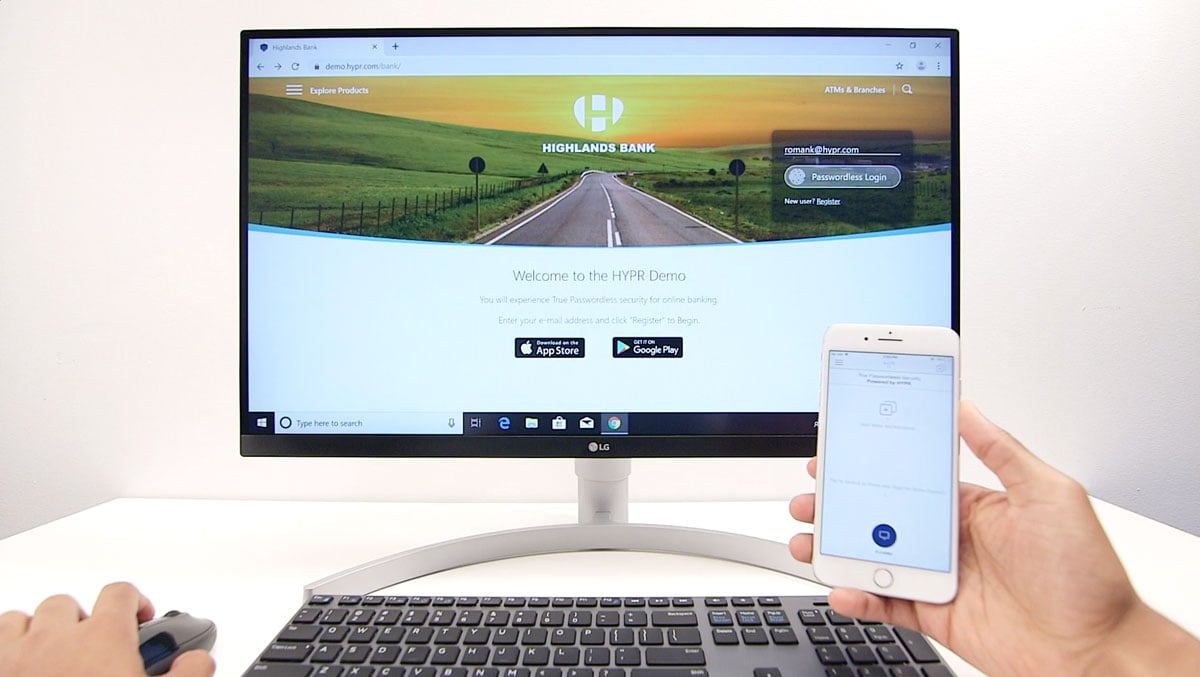
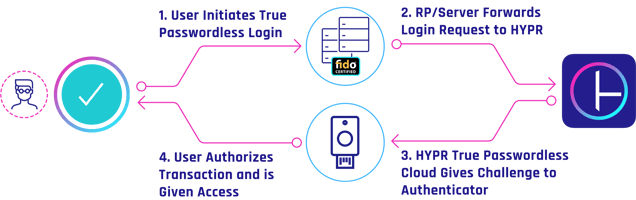
FIDO-enabled services work by asking users to select one of several available authenticators, to then generate a public/private key pair. The public key is shared with the desired service, which then sends an encrypted challenge. The user digitally signs that challenge and verifies their identity. This methodology is often referred to as "True Passwordless" — where the user experience is familiar, but the underlying architecture is very different.
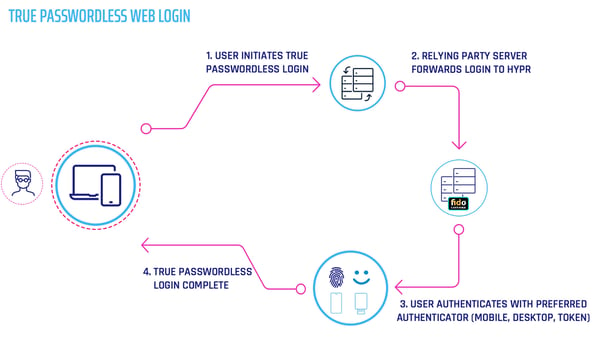
Organizations looking to migrate to a passwordless user experience should seek a partner that provides true passwordless multi-factor authentication, and can secure mobile, web, and desktop. HYPR is an example of a passwordless platform that is focused on this level of cross-platform functionality.
What are some advantages of using a FIDO2 mobile and web platform?
- Rapid time to value by focusing on devices your users already possess (e.g. smartphones, laptops)
- Excellent commercial vendor options available for buyers
- Provide integration of common passwordless methods including FIDO2 and biometrics
- Provide SDK support to enable extensibility for local systems and applications
- Interoperable with authentication plugins from commercial identity vendors
- Enable expert support partnership for enterprise authentication teams
See a demo of a mobile-to-web login powered by a FIDO2 authentication:
FIDO2 Security Tokens
A popular passwordless method is the use of a hardware security token. The general idea is the same as using a smartphone only the client authenticator is a key fob, USB token, or a hardware dongle. YubiKey is a good example of a FIDO2 passwordless experience.
The underlying flow is very similar to other FIDO authentications, relying on a PKI handshake where clients provide a locally generated public key to a server as the basis for a subsequent authentication challenge. In some high-assurance environments such as public sector or financial services there may be a requirement to use a hardware token to generate a private key for this PKI handshake.
An organization would typically select and deploy their preferred FIDO hardware token to their users. However, the interoperability of the standard means that most users can utilize any FIDO-Certified token for this authentication. This is a key benefit of FIDO2 tokens. Unfortunately mass adoption has been slow, with enterprises citing additional hardware costs, logistics of distributing tokens, and user experience concerns as key factors.
For maximum control and visibility an organization might choose to deploy a platform approach to manage, provision, and deploy FIDO2 security tokens. By leveraging an authentication platform such as HYPR, organizations can leverage smartphones and security tokens as interoperable authenticators for their passwordless initiatives.
What are the advantages of using FIDO2 security token for passwordless authentication?
- Hardware-based security keys achieve a higher level of assurance, especially when used in conjunction with MFA
- Defined by open specifications that encourage use of strong authentication
- Open Standards managed by a large community of FIDO consortium vendor participants such as Microsoft, Google, HYPR, and others
- Reliably evolving from FIDO to FIDO2 as computing technology progresses
- Security protection is built on a mature public key technology foundation
Windows Hello Passwordless
Microsoft has created a biometric authentication method for Windows 10 called Windows Hello that allows users to validate their identity with a biometric sensor – thus removing the need for a login password.
Windows Hello is Microsoft's paswordless login method for personal use and comes with most Windows 10 machines.
Windows Hello for Business (WHfB) is the edition used for enterprise access.
Both versions support multiple biometric modalities such as fingerprint, facial, iris, or retina scan.
Setting up Windows Hello is straightforward and usually happens upon a workstation's initial boot. Users set up the process in the sign-in options under their account settings by registering their biometric. Once done, they can access Microsoft accounts and applications without having to enter a password.
When enabled, Windows Hello offers the user multiple options at the login screen:

A key feature of Windows Hello is the use of cutting-edge biometric sensors such as Intel RealSense cameras. The technology works via 3D structured light alongside anti-spoofing methods to reduce the likelihood of impersonation. The system works for users with Microsoft accounts as well as other services (non-Microsoft) that support FIDO authentication.
As one would expect, Windows Hello was designed for both enterprise and consumer use – and it appears to be popular in both environments. Microsoft recently stated that more than 150 million people were using passwordless authentication on Windows each month.
Enterprises often use Windows Hello alongside passwordless authenticators such as a mobile app and security token. Windows Hello provides an excellent choice as a primary or secondary authenticator, especially in cases when users lose or forget their smartphone.
What are some advantages of Windows Hello for Passwordless Authentication?
- Integrated into the Microsoft Windows 10 operating system
- Designed to support FIDO specifications for open authentication
- Supports use of biometric validation with facial, iris, and fingerprint recognition
- Dramatically reduces need for password to access operating system and applications
- Includes anti-spoofing methods to improve accuracy and avoid fraud
Is Windows Hello multi-factor authentication (MFA)?
This question is often asked by businesses as it remains unclear if the use of Windows Hello is inherently "multi-factor." While it offers a strong passwordless authentication, the Windows Hello authentication does take place locally on one device. Enterprise security teams have hesitated to refer to this as a traditional MFA as it does not require an additional device or an out-of-band authentication. For this reason organizations often use Windows Hello as a component of their authentication strategy, but rarely is it the sole primary authenticator.
Smart Cards
A smart card offers credit-card sized convenience for electronic identification, authentication, and authorization to resources. They are sometimes contactless and can include functions such as data storage and application processing. The most common use of smart cards is for personal identification, national population identification, financial services transaction enablement, and even mobile device processing (SIM cards are a form of smart card).
Smart cards have been used for many years to enforce additional step-up or strong authentication. They are particularly popular in the public sector. They are common in federal agencies, and in high-assurance environments.
Smart cards work via an embedded integrated circuit that operates like a small computer with a microprocessor and memory. Most people think of smart cards in the context of their associated readers through with direct physical contact is made. Many smart cards work through a remote interface with contactless operation via radio signaling. Such design greatly extends the potential use case options for smart cards.
What are some advantages of Smart Cards for Passwordless Authentication ?
- Offers credit-card sized convenience for users
- Well-suited for personal identification systems including national databases
- Extensible to support adjunct storage and processing (such as in a SIM card)
- Includes near field contactless operation through radio interface
- Supports many familiar use cases for business and consumer users