Stay ahead of the curve with the latest news, ideas and resources on all things Identity Assurance and Passwordless.
How to Prevent Vishing Attacks Targeting Okta and other IDPs
Highlights:
- Modern “MFA bypass” attacks are session and workflow compromises, more commonly triggered through voice phishing (vishing).
- Vishing is increasingly used to synchronize victims with real-time phishing infrastructure, dramatically increasing success rates.
- Attackers leverage valid MFA completions to capture session tokens, enroll new authenticators, or abuse help desk recovery flows.
- Defending against vishing-driven MFA bypass requires phishing-resistant authentication and hardened identity controls.


Vishing as the Front Door to MFA Bypass
Threat reporting tied to ShinyHunters and Scattered Spider-linked activity shows voice phishing (vishing) being operationalized as a coordinated access vector against enterprise identity systems.
Rather than relying solely on email-based phishing, attackers now call employees directly, impersonating IT support, security teams, or identity administrators. These calls are not random — they are tightly coupled with live phishing infrastructure and identity workflows.
The goal is not to “steal a password”; it is to walk the victim through a legitimate authentication event while the attacker intercepts the outcome.
This is why legacy MFA continues to “work,” yet organizations are still getting breached.
Attack Pattern 1: AiTM + Vishing-Coordinated Session Hijacking
The most common technical foundation of MFA bypass is the Adversary-in-the-Middle (AiTM) attack, often delivered through frameworks like Evilginx.
Vishing is used to initiate and synchronize the attack.
How It Works
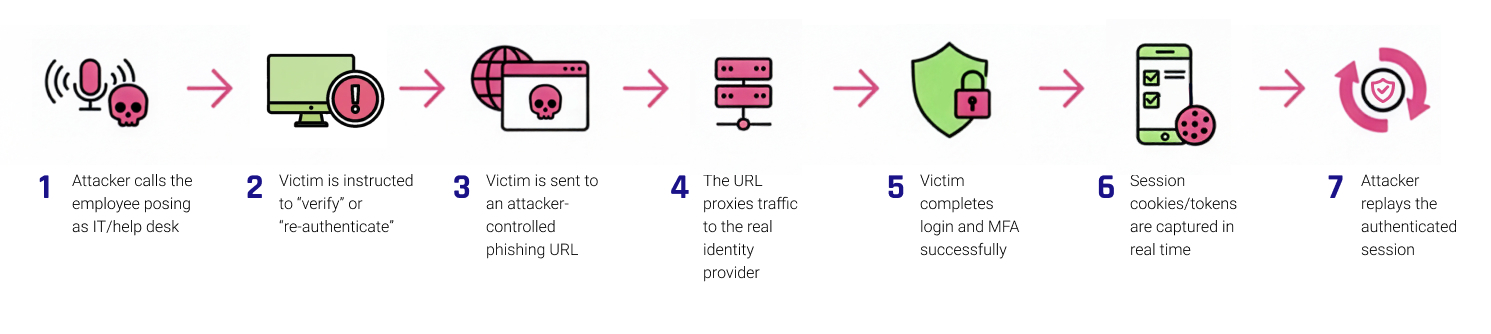
- Attacker calls the employee posing as IT/help desk
- Victim is instructed to “verify” or “re-authenticate”
- Victim is sent to an attacker-controlled phishing URL
- The URL proxies traffic to the real identity provider
- Victim completes login and MFA successfully
- Session cookies/tokens are captured in real time
- Attacker replays the authenticated session
The user never fails MFA. The IdP never raises an error. And access is granted to the attacker.
Why MFA Doesn’t Stop This
Legacy MFA validates the user at the point of authentication. It does not protect bearer session tokens after issuance. Once a session exists, possession equals access.
Attack Pattern 2: Real-Time MFA Interception via Voice Pretexting
Threat groups linked to Scattered Spider, LAPSUS$, and ShinyHunters have operationalized vishing as a way to control victim timing.
Instead of hoping a user clicks quickly, attackers keep the victim on the phone while guiding them through the login flow step by step.
How It Works
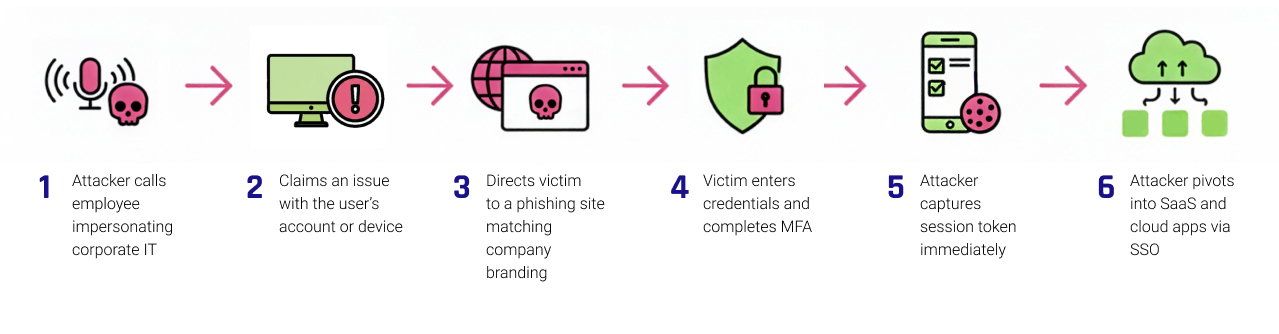
- Attacker calls employee impersonating corporate IT
- Claims an issue with the user’s account or device
- Directs victim to a phishing site matching company branding
- Victim enters credentials and completes MFA
- Attacker captures session token immediately
- Attacker pivots into SaaS and cloud apps via SSO
This works because the interaction feels procedural, not suspicious. From the victim’s perspective, this is a normal support interaction.
5. Attack Pattern 3: Vishing-Driven Help Desk and MFA Reset Abuse
Not all MFA bypass involves phishing infrastructure.
Many attacks target account recovery and help desk workflows, using vishing to bypass identity verification.
How It Works
- MFA reset or factor removal
- Enrollment of attacker-controlled authenticators
- Issuance of temporary access codes
- Bypass of identity verification checks
These attacks succeed because identity is treated as a process. When verification relies on knowledge-based or procedural checks, voice impersonation is often enough.
Account recovery and MFA reset flows must require entire identity verification orchestration, not conversational validation. That means binding recovery actions to step-up identity proofing that verifies the person behind the action, not just their answers. If reset workflows cannot attest to the user’s identity and device context at the point of reset, they remain a significant weakness in enterprise workflows.
Attack Pattern 3: Vishing-Driven Help Desk and MFA Reset Abuse
Not all MFA bypass involves phishing infrastructure.
Many attacks target account recovery and help desk workflows, using vishing to bypass identity verification.
Common Outcomes
- MFA reset or factor removal
- Enrollment of attacker-controlled authenticators
- Issuance of temporary access codes
- Bypass of identity verification checks
These attacks succeed because identity is treated as a process. When verification relies on knowledge-based or procedural checks, voice impersonation is often enough.
Account recovery and MFA reset flows must require entire identity verification orchestration, not conversational validation. That means binding recovery actions to step-up identity proofing that verifies the person behind the action, not just their answers. If reset workflows cannot attest to the user’s identity and device context at the point of reset, they remain a significant weakness in enterprise workflows.
Five Ways to Defend Against Vishing and Modern MFA Bypass
Defensive Controls That Actually Break the Attack Chain
Stopping vishing-driven MFA bypass requires eliminating interceptable authentication paths, not adding more prompts.
1. Deploy phishing-resistant authentication (FIDO2/passkeys)
Device-bound, passkey-based authentication prevents AiTM proxies from replaying sessions.
2. Reduce reliance on push and OTP-based MFA
These factors are inherently vulnerable to real-time interception and social engineering. Retire push approvals and one-time codes for high-risk access and account modification workflows.
3. Harden help desk and recovery workflows
Account recovery must be treated as part of the identity perimeter, with strong, deterministic identity verification. MFA resets, device changes, etc should require dynamic identity orchestration workflows - not procedural validation.
4. Enforce session-aware access controls
Authentication is a point-in-time event; access is continuous. Implement controls that detect anomalous device shifts, token replay, impossible travel, and abnormal post-auth behavior that revoke access in real time.
5. Detect rapid post-auth SaaS pivots
Compromised sessions are typically followed by immediate access to Microsoft 365, Salesforce, Slack, and other federated applications. Monitor for unusual application access patterns immediately after authentication and restrict lateral movement.
Key Takeaways for Vishing Prevention
- Vishing is now a primary enabler of MFA bypass attacks
- Most MFA bypass incidents involve stolen or replayed sessions - not broken MFA factors
- Real-time voice interaction dramatically increases attacker success
- Defenses must focus on phishing resistance and post-auth control, not user awareness
Conclusion
Modern MFA bypass must be treated as an access control problem, not a user behavior problem.
As long as access is granted based on a single successful authentication event, attackers will continue to use vishing to trigger legitimate logins and hijack the resulting sessions. Stopping these attacks requires securing access differently — not retraining your help desk, or putting your end users through more security modules.
Defensive strategy must shift to phishing-resistant authentication and context-based attestation, where access is always bound to the user, device, and environment. If access cannot be proven in context, it should not be granted.
Subscribe to our updates to receive expert insights and learn how HYPR's multi-factor verification and digital identity solutions can protect your business and customers.
Anton Gurov
CISO
Anton Gurov currently serves as HYPR's CISO, focusing on Security, Compliance and Operations. Anton’s industry background is in mobile payments, ad tech and cloud management, with direct experience in PCI-DSS/SOC2/ISO/GDPR/CSTAR compliance in private/hybrid and cloud-native organizations. His career contributions led to 3 successful startup exits totaling $1.1B+. Anton had exposure to NIST standards and controls while pursuing FedRAMP at VMware.
Related Content
